FAQ
General
What information does freavo require from me?
What personal data is stored by freavo?
Technology
How does freavo work from a technical standpoint?
Which attacks does freavo protect me from?
Are there any backdoors in freavo?
Where is my crypto-key stored?
Usage
How do I create an account for freavo?
On which platforms is freavo available?
Why do I need a freavo account? What does it consist of?
In order to get calls and messages, does freavo have to be running all the time?
I forgot my password? What can I do now?
Why should I backup my crypto-key?
Why do I have to enter a password, when I backup my crypto-key?
Is the password for my crypto-key the same as for my account?
My device is no longer accessible. How do I use my account on another device?
If I have any troubles, what can I do?
What is freavo?
freavo is an Internet telephony solution with focus on security, especially privacy protection. It is based on the popular Voice over IP standard SIP and uses state of the art encryption methods to prohibit government agencies (NSA and its relatives) or bad guys from listening in to your call. In times like these where surveillance is all-around, freavo can give you back the sovereignty over your communication.
What information does freavo require from me?
freavo does not ask for any of your personal information for registration. Optionally, you can insert your E-Mail address to verify your public key at the server to avoid malicious activities during the registration process. freavo does not collect, monitor, or share any of your data.
What personal data is stored by freavo?
freavo does not store any personal data or meta-data.
How does freavo work from a technical standpoint?
At its core, freavo features a Voice over IP implementation with well-known and frequently used protocols SIP (Session Initiation Protocol) and RTP (Real-Time Transport Protocol). Whilst utilising many advantages of those protocols like flexibility or scalability, a major drawback of those protocols - limited security features - has been addressed by the implementation of our security layer. Located between SIP/RTP protocols and network access via IP, this layer ensures, that every piece of information generated by or addressed to the application is secured. At application's first communication attempt, the security layer establishes a secure channel with our server using EC-FHMQV (authenticated key exchange) and AES-GCM (authenticated secure channel using short-term session keys). These encryption methods feature Perfect Forward Secrecy (PFS), whereas a potentially disclosed private encryption key will not allow any subsequent decryption. The server will, for example, help to find subscribers and initiate Voice over IP calls, after which a similar, but independent EC-FHMQV and AES-GCM based short-term channel is created directly between the two communication partners. Any voice or payload information is transferred using this end-to-end channel, leaving even our server unable to obtain any payload information, restricting the server to the role of a call broker.
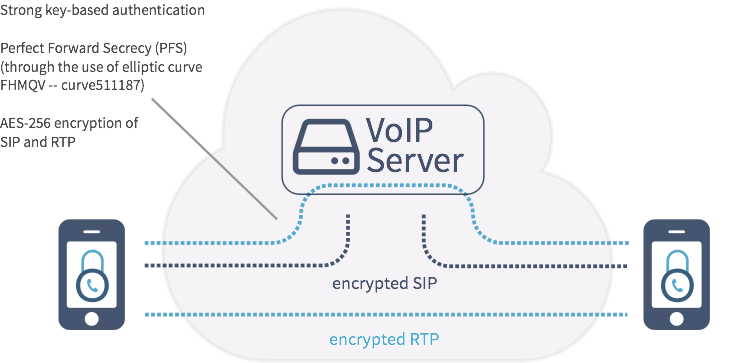
Which attacks does freavo protect me from?
Our promise to provide secure communication is based on extensive, long-term research and development in the field of IT-security and Voice over IP. The outcome of this is a construct of state-of-the-art cryptography paired with well-established Voice over IP technology. Despite of SSL/TLS based VoIP security features, our cryptography conception stipulates the implementation of a security layer, which features elliptic curve cryptography to provide end-to-end encryption, leaving only the legitimate communication partners able to communicate. Hence, establishing your civil right of private communication.
Are there any backdoors in freavo?
The threat of backdoors is more prevalent nowadays than ever. We don't have any intention or interest on approving or even participating in such methods. Additionally, under Austrian law it is not allowed to install backdoors on political or governmental basis.
Where is my crypto-key stored?
Your crypto-key is stored in your mobile device only. It is created there and is never being transferred on any network. With exporting crypto-key information form the application, the crypto-key can be stored to a separate file on your device. In this case the key information is secured using encryption methods, which can not be decrypted without authenticating to our server.
How do I create an account for freavo?
Simply install the application from Google Play Store or download it from the FREAVO homepage. On first start, your personal encryption keys are generated and you can create an account using the "Account Setup Wizard". A registration confirmation will be sent to the provided email address.
On which platforms is freavo available?
We support Android devices only. A version for non-Android devices is not (yet) available.
Why do I need a freavo account? What does it consist of?
An account can be considered to be your identity within the freavo network. It consists of your account number, which is also the number on which you are reachable within the network, a password, which you would need to re-register, and your personal crypto key information.
In order to get calls and messages, does freavo have to be running all the time?
If you want to be reachable from the freavo network, you have to have the application started.
I forgot my password? What can I do now?
We do not provide any automatic password recovery mechanism. You can contact support@freavo.org instead.
Why should I backup my crypto-key?
Your device is the only place where your crypto-key is stored. When your device becomes inaccessible to you, this file can help to recover your account to another device.
Why do I have to enter a password, when I backup my crypto-key?
The purpose of this password is to preserve your account in case the file is disclosed. This password is not stored on any server and is incorporated to cryptographic functions protecting the export file. This password can not be recovered by any means, so please remember it.
Is the password for my crypto-key the same as for my account?
No, it is not. If you decide to, you can use the same password for both cases, although we advise not to use the same password.
My device is no longer accessible. How do I use my account on another device?
After re-installing the application from another device, import the crypto-key file and provide your Login details, which both can be done during "Account Setup Wizard". It is required to have the crypto-key file exported from your former devices. As private crypto-key information is stored only on your devices, the account can be re-accessed only if this file is available.
If I have any troubles, what can I do?
If you can't find any solution to your problem in FAQ, please contact as at support@freavo.org

